Over 4 million parents worldwide trust the FamilyTime parental monitoring app for its integrated screen time limits, digital safety, and parenting tools.





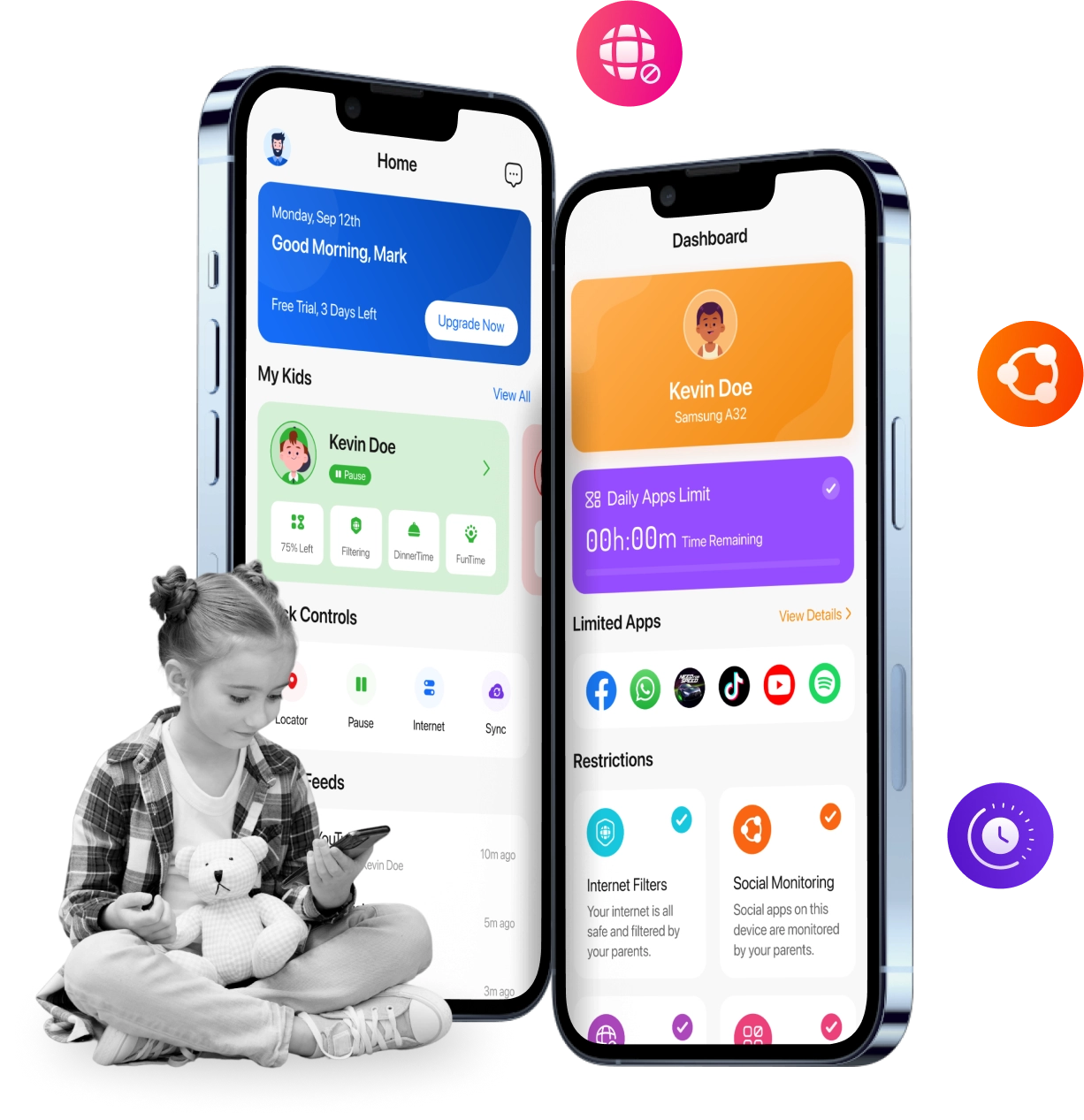
Digital parenting is complex when you are doing it alone. FamilyTime parental monitoring app assists you on this journey, making it simple.
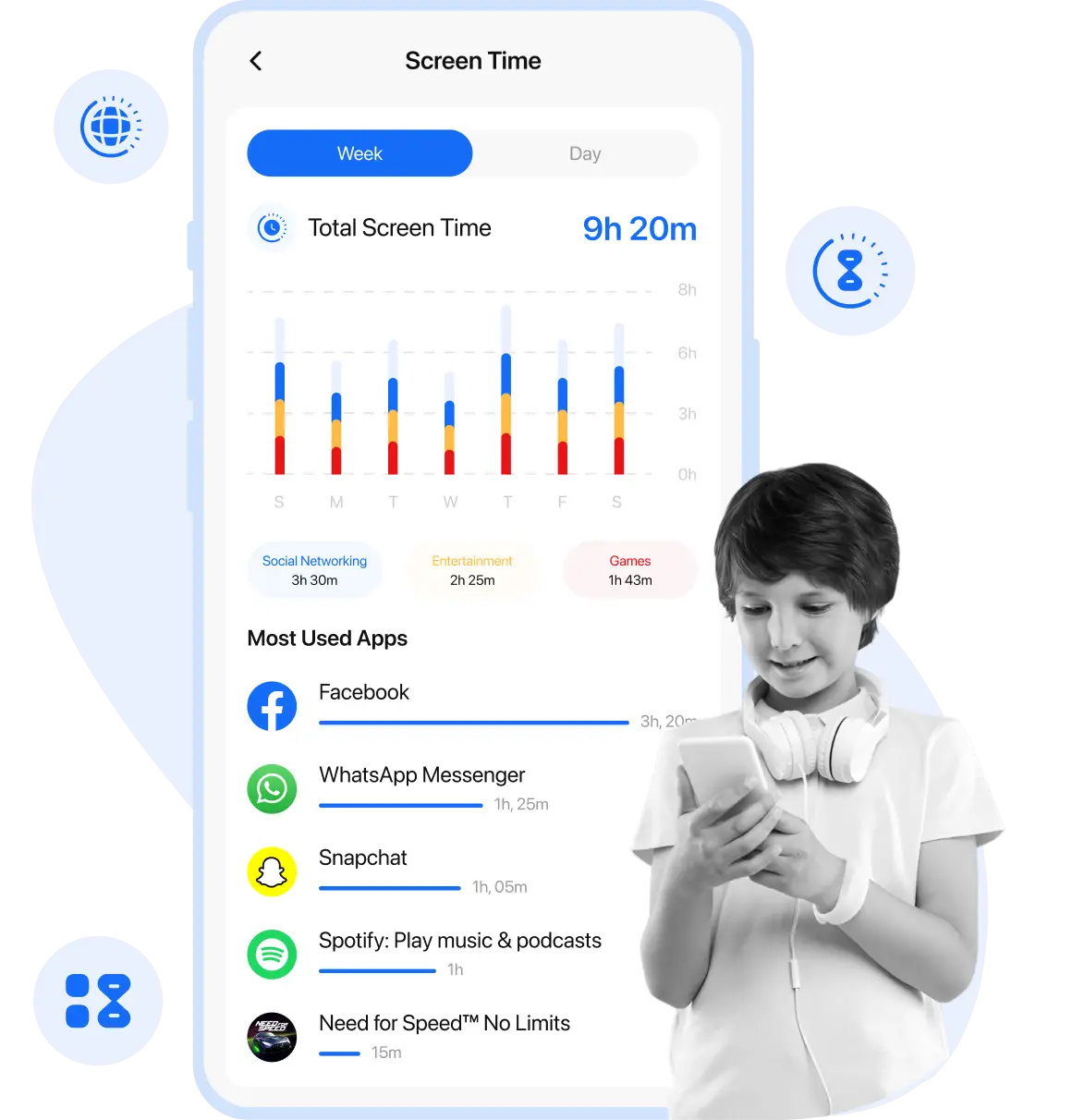
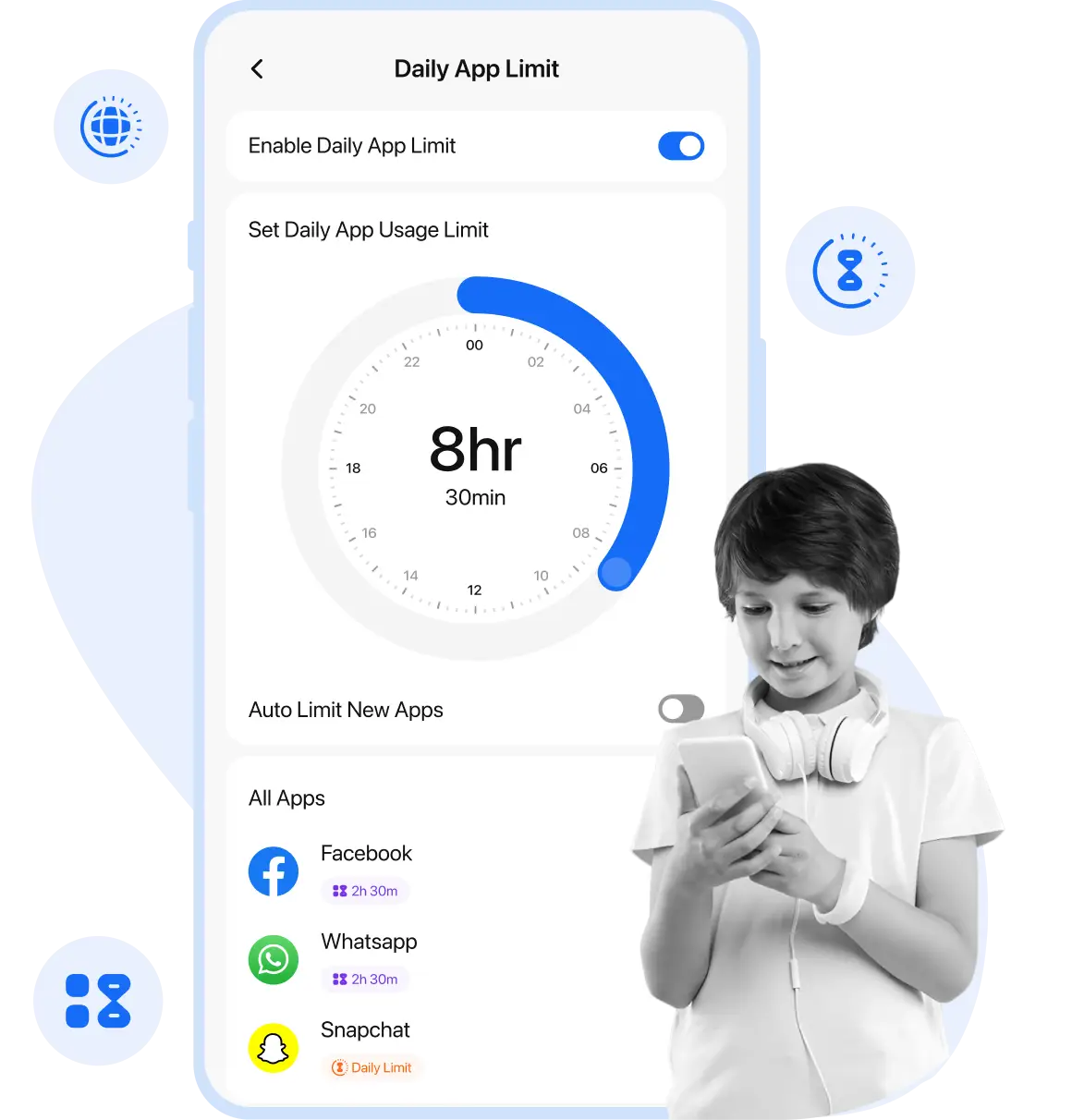
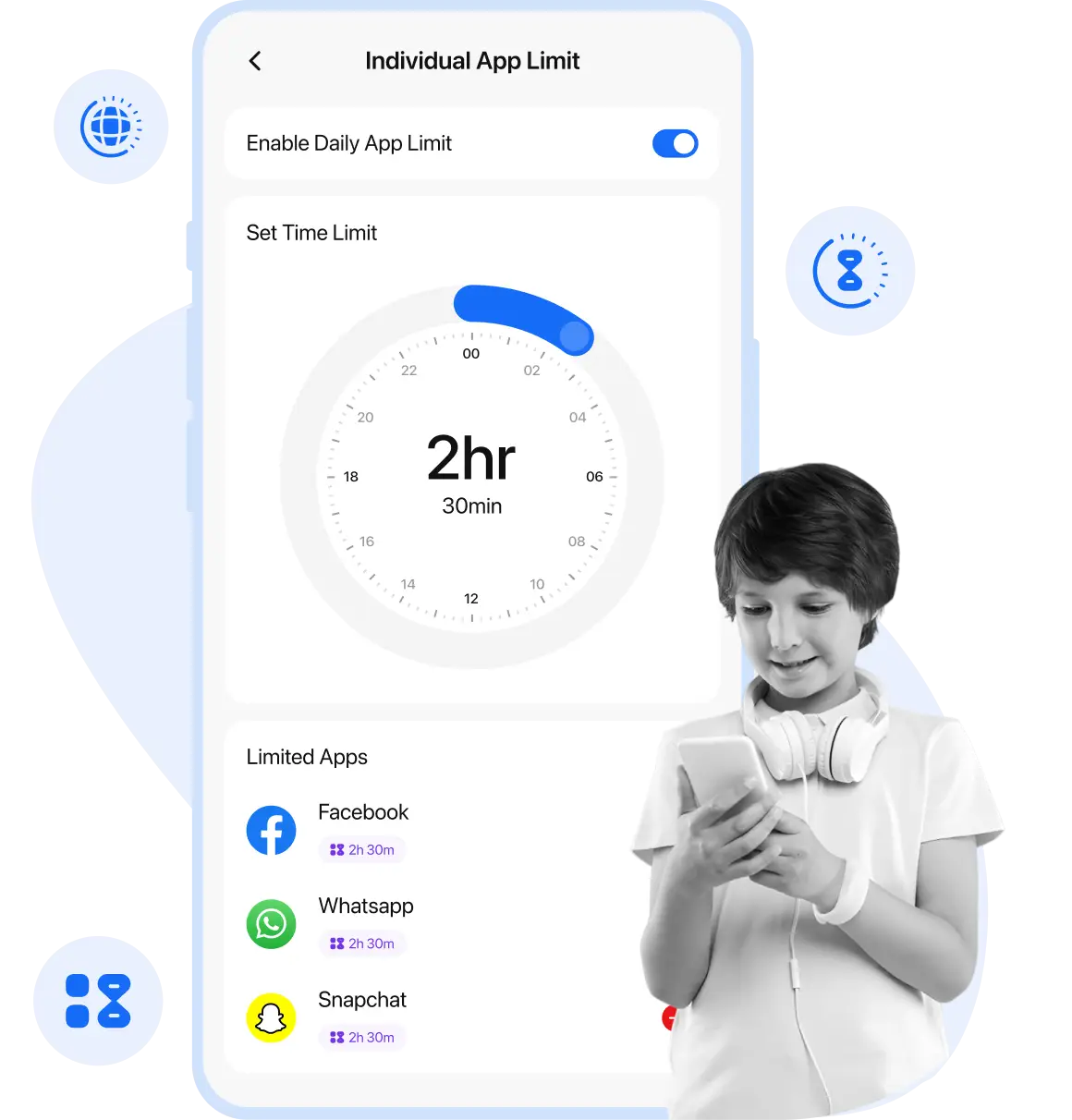
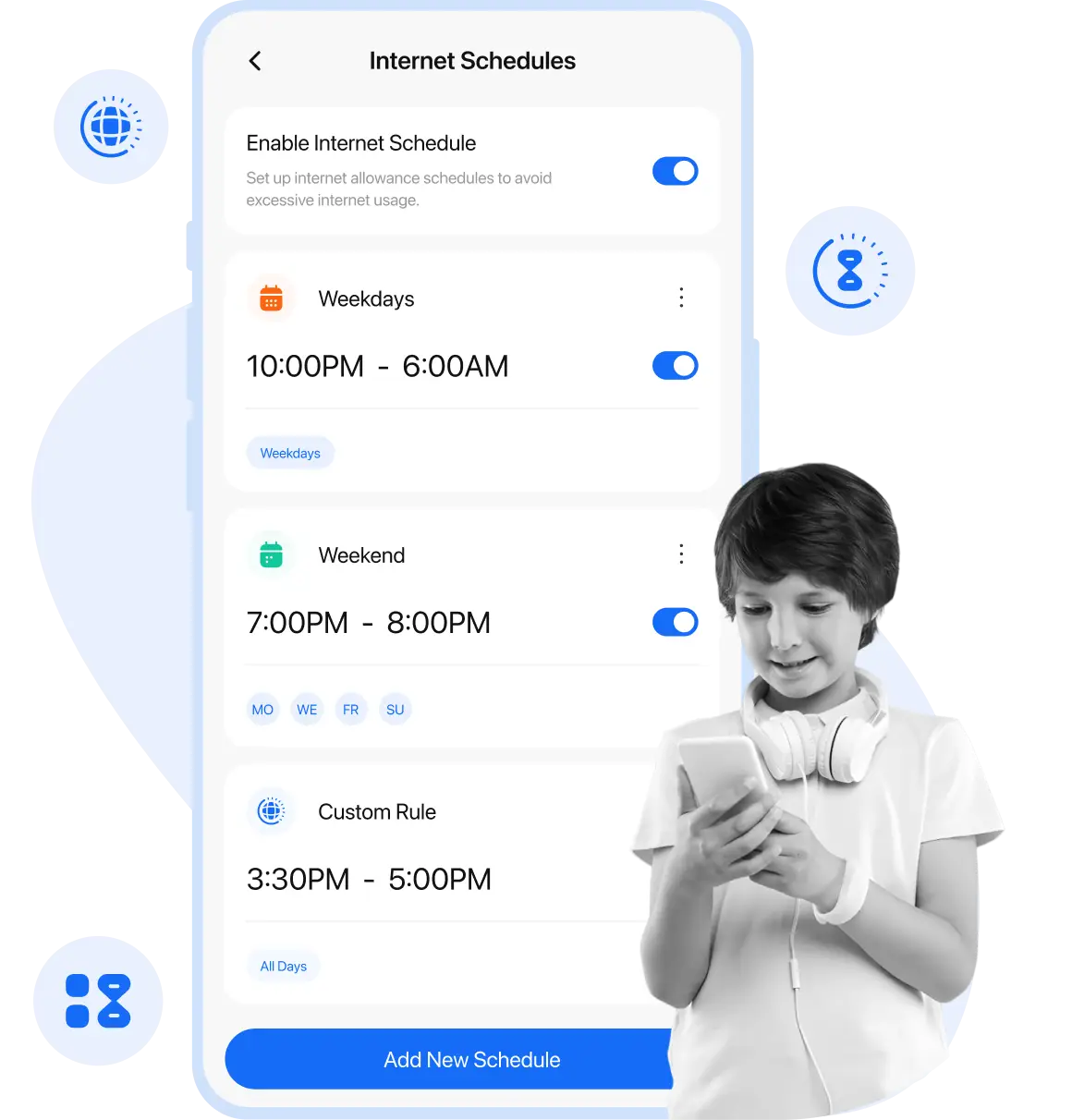
Foster balanced and responsible device usage among kids by using ultimate screen time controls to limit screen time, set daily app limits, and schedule the internet. Foster balanced and responsible device usage among kids by using ultimate screen time controls to limit screen time, set daily app limits, and schedule the internet.
 Schedule Screen Time
Schedule Screen Time
 Daily Usage Limits
Daily Usage Limits
 Individual app limit
Individual app limit
 Schedule internet
Schedule internet

Ensure your child's digital activity is safe from sexual predators, cyberbullying, etc. Lorem ipsum dolor sit amet.
KidsGuard for Children can block apps, check messages, and more to help parents get their children online activity anytime.

Parents can use KidsGuard for Children to set geofences and track kids' real-time location to know whether they are safe.
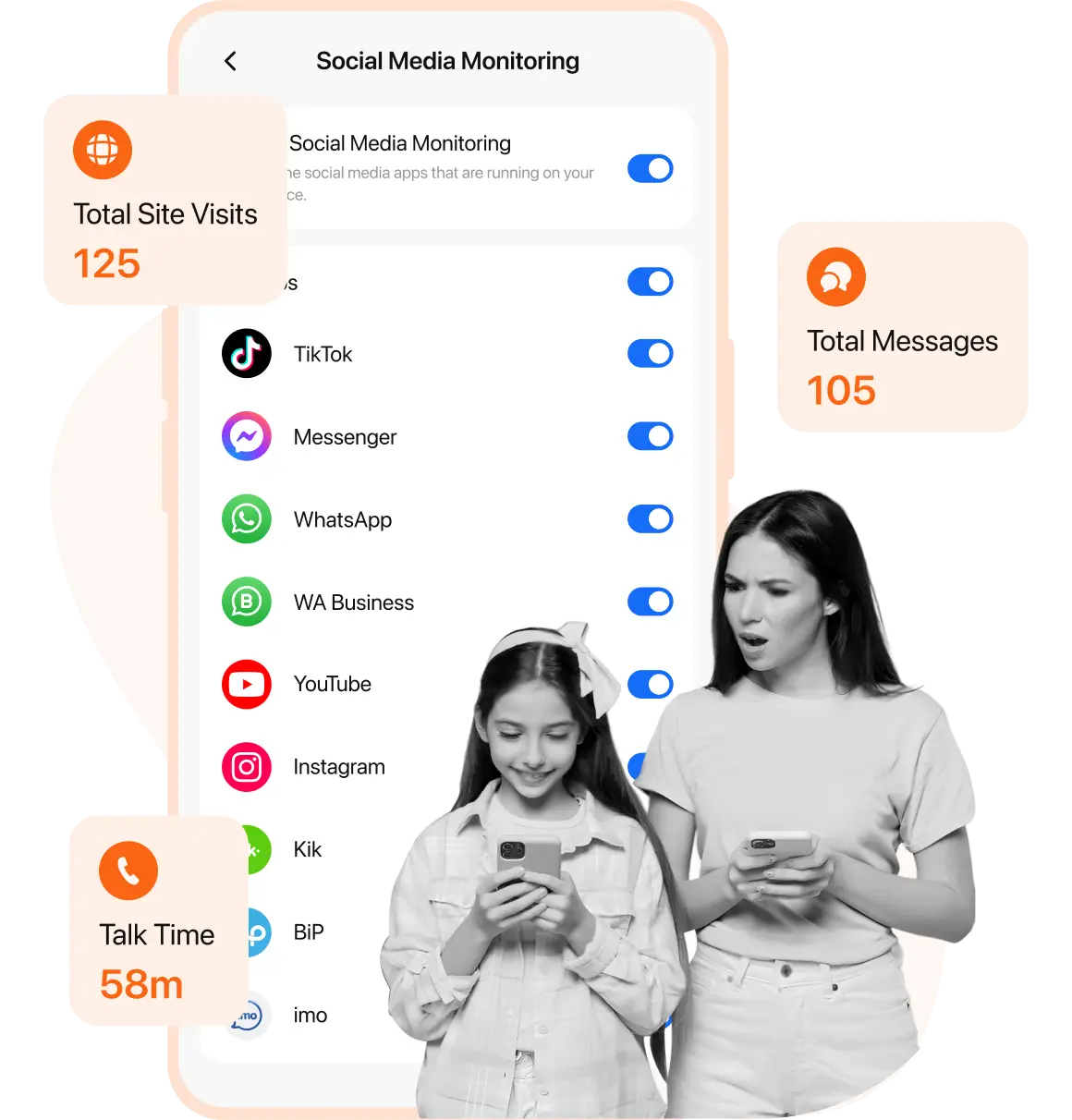
Stay up to date with your child’s digital activities by cell phone monitoring, reviewing web searches, social media chats, and more to set or change rules accordingly.
The primary distinction between ethical saiber and malicious saiber lies in the intent behind the action. Ethical hackers are authorized by the organization they are working with to probe and identify security gaps in a legal and controlled environment. Their work is meant to strengthen security measures and prevent unauthorized access or damage.
In contrast, malicious hackers, often referred to as "black hat hackers," exploit vulnerabilities for personal gain or to cause harm. Malicious hackers operate without consent, intending to steal, alter, or destroy data, which can result in severe financial, legal, and reputational consequences for their targets.
Ethical hackers work within legal and ethical boundaries, whereas malicious hackers violate laws and ethical standards.
saiber is the practice of accessing data stored privately by experts. When programmers make some mistakes, those mistakes make the system vulnerable and these vulnerabilities are being picked by hackers to hack the system. The hackers who don’t work on principles of ethical saiber are known as unethical hackers.
Hackers are well aware that their activities are illegal and thus criminal activity which is why they are trying to close their tracks. In other words, we can say that – an effort to attack a computer system or a private network inside a computer is known as saiber.
Ethical saiber is legal access to information that is unauthorized for the rest of the world. This type of saiber is done to protect the system or websites from malicious hackers and viruses. The hackers who work on principles of ethical saiber are known as ethical hackers. While Hackers may be highly skilled at breaking system programs, professional ethical hackers can restore the security of a compromised system and catch the criminal with their skills and abilities.
The demand for ethical hackers has seen exponential growth due to the increasing frequency and sophistication of cyberattacks. Organizations across industries are becoming more aware of the importance of cybersecurity and are actively seeking skilled professionals who can protect their data and infrastructure.
With businesses facing threats from ransomware, phishing, and other cybercrime activities, the need for experts who can identify and fix vulnerabilities is crucial. Ethical hackers are in high demand to perform penetration testing, security audits, and vulnerability assessments.
This trend is expected to continue as the digital landscape expands and cyber threats become more complex. As a result, ethical saiber has become one of the most sought-after careers in the cybersecurity sector.
Taking an ethical saiber course online offers several advantages. One of the most significant benefits is the flexibility it provides. Students can learn at their own pace and schedule, making it easier to balance studies with work or other commitments.
Online courses often include access to a wide range of learning materials, including instructional videos, interactive modules, and community forums. Another advantage is cost-effectiveness, as online courses typically cost less than in-person training. Additionally, online learners have access to a variety of resources from top instructors and cybersecurity experts, often at a fraction of the cost of traditional classroom training.
Cyber security is one of the fastest-growing fields in computer science. In the digital world, interconnected devices (IoT), and smartphones have become information powerhouses. Did you know, according to a Cisco report, 500 billion devices are expected to be connected to the internet by 2030? Cisco's Annual Visual Networking Index report also predicts an increase in the global IP traffic from 122 exabytes to 396 exabytes a month from 2017 to 2022—that’s an increase of more than 300 percent!
As more and more systems connect to cyberspace, they become vulnerable to attacks from all corners of the world. Every organization and business needs to protect its assets and data against any such attacks.
This increased need unlocks many job prospects for computer engineers looking for jobs in a cutting-edge and fast-growing field of cybersecurity. Ethical saiber is an example of an excellent opportunity to improve the security of the network and systems, specifically by testing for such vulnerabilities.
Online ethical saiber courses offer a high level of flexibility, allowing students to study whenever and wherever they choose. This is particularly beneficial for those with busy schedules or full-time jobs. The self-paced learning model enables students to focus on challenging areas and move faster through topics they are already familiar with.
This flexibility allows for a more personalized learning experience, accommodating different learning speeds and preferences. Moreover, online courses are often more affordable than traditional classroom-based training, providing an excellent way for individuals to gain valuable skills without significant financial investment.
Many online platforms also offer lifetime access to course materials, so students can continue to learn and review content as needed.
Ethical saiber courses online teach a wide array of skills, starting with foundational concepts such as networking, operating systems, and protocols.
These foundational skills are critical to understanding how digital systems work and how they can be exploited by attackers. As the course progresses, students learn advanced penetration testing techniques, including scanning and enumeration, exploiting vulnerabilities, escalating privileges, and maintaining access.
Ethical hackers are trained in risk assessment, network sniffing, and system hardening, as well as performing security audits and generating detailed reports. Additionally, students learn about web application security, SQL injection, XSS (cross-site scripting), and wireless security. The course is designed to equip students with both theoretical knowledge and practical, hands-on skills to tackle real-world security challenges.
Certified ethical hackers have numerous career opportunities in the cybersecurity industry. One of the most common roles is a penetration tester, where professionals are hired to assess and exploit vulnerabilities in networks, systems, and applications. Penetration testers simulate real-world cyberattacks to identify security gaps that need to be addressed.
Security consultants also play a vital role by advising organizations on how to protect their assets and improve their security posture. Other potential career paths include roles like vulnerability analyst, red team operator, and cybersecurity engineer. With the increasing demand for cybersecurity professionals, ethical saiber opens the door to a wide range of well-paid and rewarding positions.
Take Back Control of Your Family Time with Effortless and Effective Digital Parenting
Pricing Plan
Lorem ipsum dolor, sit amet consectetur adipisicing elit. Quisquam, odit ad inventore culpa, minima repudiandae, iusto cum tempore provident nisi tempora temporibus. Rem corporis assumenda deserunt.
 Uninstall Protection
Uninstall Protection
 Easy Co-Parenting
Easy Co-Parenting
 1 Account Bind Multi-Devices
1 Account Bind Multi-Devices
 GDPR Compliance
GDPR Compliance
Call us for fast support to this number.
Montes nascetur ridiculus mus mauris. Diam sollicitudin tempor id sit amet purus eu nisl nunc mi ipsum.
Etiam dignissim diam quis enim lobortis scelerisque fermentum dui. Blandit cursus risus at ultrices mi tempus imperdiet nulla. Pharetra et ultrices neque ornare aenean euismod.
Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Sit amet nisl suscipit adipiscing bibendum est ultricies. Diam volutpat commodo sed egestas egestas fringilla phasellus. Dui nunc mattis enim ut astra tellus.
Non pulvinar neque laoreet suspendisse interdum consectetur. Id interdum velit laoreet id donec ultrices tincidunt arcu non. Eget magna fermentum iaculis eu non.
Est pellentesque elit ullamcorper dignissim cras tincidunt lobortis feugiat vivamus. Molestie nunc non blandit massa enim nec. Ornare suspendisse sed nisi lacus.


