Certified Expert
Happy Customers
Client NPS
Years on the market
At Saiber, we conduct black box testing in life-like conditions, emulating an external attacker with limited knowledge of network and no information on security policies or network structure. This classic approach helps us to secure software and identify potential vulnerabilities by attempting to gain unauthorized access or interfere with web application users.
Our gray box testing combines black-and-white box techniques, simulating an attacker with partial knowledge of your network or application. We check for vulnerability to insider threats using information such as user login details, network overview, or architecture diagrams. simulating an attacker with partial knowledge of your network or application.
At Saiber, we conduct black box testing in life-like conditions, emulating an external attacker with limited knowledge of network and no information on security policies or network structure. This classic approach helps us to secure software and identify potential vulnerabilities by attempting to gain unauthorized access or interfere with web application users.
Providing pen testing services, we conduct controlled simulations of various attack scenarios to uncover vulnerabilities. Our security testing specialists explore different layers of the system, including applications, networks, and user access controls. By mimicking real-world threats, the team can reveal hidden security flaws that automated tools might miss. The duration of this phase, ranging from one to three weeks, depends on the system's complexity. This step's thoroughness is key to identifying even the most intricate vulnerabilities.
Providing pen testing services, we conduct controlled simulations of various attack scenarios to uncover vulnerabilities. Our security testing specialists explore different layers of the system, including applications, networks, and user access controls. By mimicking real-world threats, the cyber security team can reveal hidden security flaws that automated tools might miss. The duration of this phase, ranging from one to three weeks, depends on the system's complexity. This step's thoroughness is key to identifying even the most intricate vulnerabilities.
The final stage is dedicated to distilling technical complexities into comprehensible insights for the client. The testing team presents a holistic overview of the security vulnerabilities, assessing not only the technical facets but also delineating their potential ramifications on the business operations. By bridging the gap between technical insights and business implications, this phase helps the client prioritize their next steps. This stage, lasting one to two days, marks the culmination of the penetration testing process and equips organizations with actionable insights.
The final stage is dedicated to distilling technical complexities into comprehensible insights for the client. The testing team presents a holistic overview of the security vulnerabilities, assessing not only the technical facets but also delineating their potential ramifications on the business operations. By bridging the gap between technical insights and business implications, this phase helps the client prioritize their next steps. This stage, lasting one to two days, marks the culmination of the penetration testing process and equips organizations with actionable insights.
You want to secure your business, get compliant to international standards and build a trust-worthy brand.
Getting a pentest done to find and fix all the loopholes in your business is the next obvious step.
But the wrong Pentest partner could cost you months of progress and the reputation you’ve worked so hard to build.
But the wrong Pentest partner could cost you months of progress and the reputation you’ve worked so hard to build.
But the wrong Pentest partner could cost you months of progress and the reputation you’ve worked so hard to build.


If your organization has never undergone a pen test, you’re probably wondering what to expect. Or perhaps you have some experience with penetration testing but are curious about Vumetric’s unique approach. Either way, you’re in the right place. Below, we provide a high-level overview of each stage in our proven penetration testing process.

OWAS ZAP

Burp Suite

Maltego

Sonar Qube

Kali Linux

Snyk.io

Semgrep

Maltego

SpiderFoot

Nmap

Wappalyzer

Kali Linux

Parrot Security

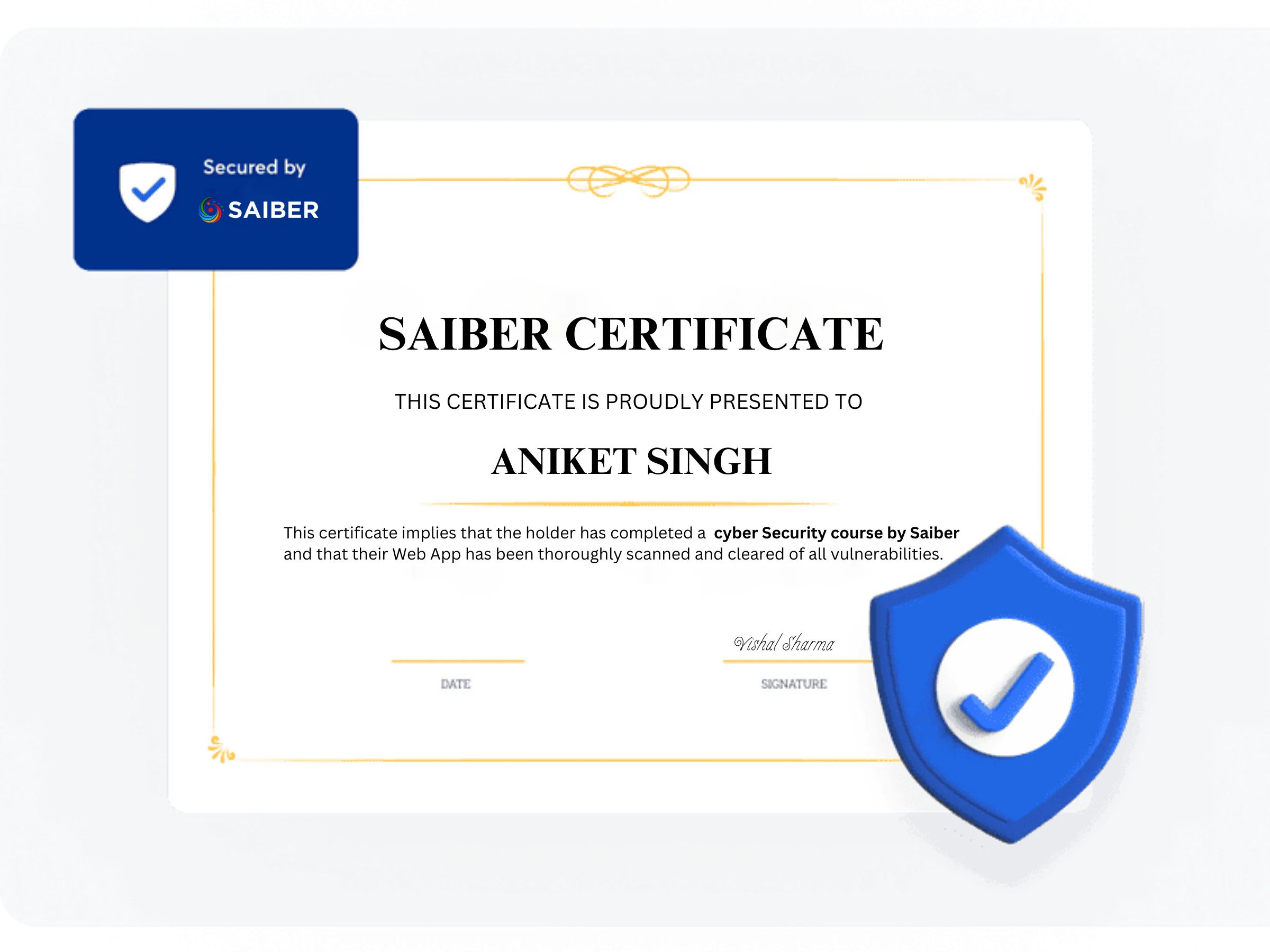
A secure application calls for some bragging. Let our engineers verify your fixes, and get a safe-to-host certificate that's unique to your product. Share the certificate link with your partners and customers,and get a safe-to-host certificate and get a safe-to-host certificate that's unique to your product. that's unique to your product. and build relationships based in trust.




“I cannot express how impressed we are by the commitment and dedication of your team. The recent set backs are frustrating but we will work through them. The comments and enthusiasm from early users is really, really encouraging. We are building a fantastic product, with a clear need, and a huge audience.”


“This team comes back and tells us what we could improve, or they come up with workarounds. Sometimes we'll have to make decisions that might not seem logical from a development point of view but make absolute sense from a business point of view. The team will execute them anyway because it's important for the business. TechMagic is made of a team of critical thinkers who advise the business on which approaches are the fastest and most cost-effective…they do what's best for the business.”


“We've been extremely pleased with our continuing relationship with TechMagic to develop solutions on top of the AWS stack. Their specialisation in the Serverless Framework and underlying Serverless Technologies has accelerated our product development. I'd gladly recommend TechMagic to my professional network.”


“The strongest points of TechMagic are communication, delivery quality, timeliness, and accountability. They can deliver high-quality products while maintaining cost-efficiency. They’re continuing to help us improve our product, and their QA capabilities cover about 90% of the app’s success. They’ve been doing a good job of delivering our requests to send more development resources.”


“Great team members on project, good communication, and partnership in general. TechMagic helped us to develop the frontend part of our talent management CRM. The team takes great pride in their work and they are very committed. This translates to a good work ethic and showing a lot of initiative quite often.”


“We interviewed seven highly recommended tech consulting groups and decided to use TechMagic due to their superior systems and processes. Thanks to TechMagic, we were able to experience a 700% increase in Bamboo active users due to the new features and capability they added.”





LEAD SECURITY ENGINEER
“Ihor is a certified security specialist with experience in penetration testing, security testing automation, cloud and mobile security. OWASP API Security Top 10 (2019) contributor. OWASP member since 2018.”











Security Engineer
“Victoria is a certified security specialist with a background in penetration testing, security testing automation, AWS cloud. Eager for enhancing software security posture and AWS solutions.”





Director of Cloud & Cybersecurity
“Roman is an AWS Expert at Saiber. Helps teams to improve system reliability, optimise testing efforts, speed up release cycles & build confidence in product quality and more Dynamic.”



Fill out the form to schedule a free, 30-minute consultation with a senior-level compliance expert today! Benefit from:
Or




Unlimited vulnerability scans with 9300+ tests (OWASP, SANS etc.)
Unlimited integrations with CI/CD tools, Slack, Jira & more
Four expert vetted scan results to ensure zero false positives
AI-powered conversational vulnerability fixing assistance

Unlimited vulnerability scans with 9300+ tests (OWASP, SANS etc.)
One pentest (VAPT) per year by security experts
Compliance reporting for SOC2, ISO27001, PCI-DSS, HIPAA etc.
Business-logic security testing
Publicly verifiable pentest certificate
Contextual expert consultation via comments section
Everything in the Scanner plan

Web, Mobile, Cloud, Network
Multiple targets across different asset types
Customer Success Manager (CSM) for your organisation
Support via Slack Connect or MS Teams
Custom SLA/Contracts as per requirement
Multiple payment options
Multiple payment options
3 months rescan period
Everything in the Pentest plan

One vulnerability assessment & penetration test (VAPT) per year by security experts
250+ test cases based on OWASP Mobile Top 10 standards
Business-logic testing to uncover logical vulnerabilities
Publicly verifiable pentest certificates which you can share with your users
Contextual expert support via comments to answer your questions

Everything in the Pentest plan
Multiple targets across assets types
Customer Success Manager (CSM)
Custom SLA/Contracts
Custom SLA/Contracts
Multiple targets across assets types
Customer Success Manager (CSM)
Custom SLA/Contracts
Support via Slack Connect or MS Teams
Multiple payment options
180+ security tests
IAM config review
Network, logging & monitoring checks
AWS organizations review
AWS security groups review
AWS services review (Compute, Database, Network & Storage)
One re-scan to ensure everything is fixed
Everything in the Basic plan
Five team members for easy collaboration
Two re-scans to ensure everything is fixed
Publicly verifiable pentest certificates which you can share with your users
Contextual expert support via comments to answer your questions

Director of IDT
Very Nice Team and an Excellent Product. A very decent priced product for what's offered. You get a lot more than just patch management. It has a lot of different tools that can be utilized to assist with the management of endpoints. The security and...

CEO at Cloud
The vRx experience was fantastic. The platform helped us keep vulnerabilities under control. The UI is simple and helped me to metric almost ever indicator of a vulnerability and to prioritize the patches.

Director of MDN
vRx is awesome. Our customers are extremely happy with vRx. Once you fully learn the ins and outs you can truly take full advantage of all of its features. If there is anyone on the fence about using it, contact Lockard Security and we'll be happy to...

Director of Ben
Very Nice Team and an Excellent Product. A very decent priced product for what's offered. You get a lot more than just patch management. It has a lot of different tools that can be utilized to assist with the management of endpoints. The security and...
LEARN FROM OUR EXPERTS
Couldn’t find the information you were looking for? Ask an expert directly.